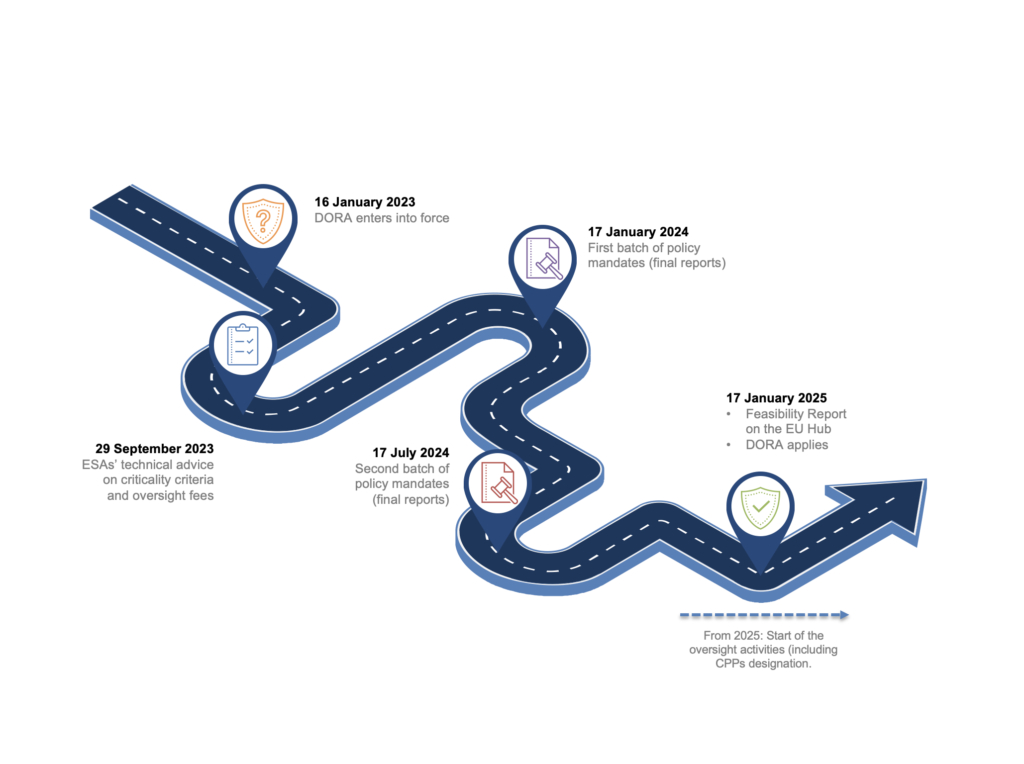
While the European Union’s (EU) Digital Operational Resilience Act (DORA) has been under development since 2020, the 2025 deadline for compliance is timely given the escalating demands for improved digital resilience. Geopolitical unrest and rising cyber threat are adding significant risks for financial institutions, making it vital to strengthen the operational resilience of the sector and ensure service continuity.
While FCA authorisation already requires financial institutions to have some level of cyber security and disaster recovery infrastructure, DORA takes it to a new level. Notably, the regulation adds both a responsibility for ICT supplier(s) performance and introduces a cross-business approach to resilience – rather than accepting the diverse plans of each isolated business unit. Furthermore, by demanding a consistent, industry-wide focus on operational uptime and security, DORA should foster a dialogue that is accelerating understanding, information sharing and innovation to create a far more consistent market-wide model.
DORA heralds a new era of digital resilience best practice – but with awareness low and less than 12 months to achieve the required due diligence and execute any potential rework, Simon Maharaj, Managing Consultant and Daniel Maw, Consultant, D2 Legal Technology (D2LT), explain why it is vital for financial institutions to place the roadmap to compliance on the board agenda today.
Critical Concern
Digital resilience is now a board level concern for financial institutions, with fears fuelled not only by the escalation in cyber threat but also the spiralling geopolitical uncertainty. Deglobalisation and conflict across both Europe and the Middle East raise new threats for all businesses, but for a financial industry that is now dependent upon digitalisation, the potential devastation associated with interference with digital systems is an extremely serious concern.
The timely introduction of European Union’s (EU) Digital Operational Resilience Act (DORA) provides a framework and guidance for organisations to manage and address ICT and cyber related risks and threats. Applying to any financial institution with a nexus within a European jurisdiction, DORA compliance must be achieved by January 2025. UK entities, in particular, will need to assess their level of DORA exposure, based on the breadth of financial markets activities included, and whether they occur in EU jurisdictions. With failure to meet DORA requirements incurring fines of up to 10 million Euros or 5% of total annual turnover, non-compliance is a significant risk for any financial institution.
Given the reputational damage and the cost associated with a breach or outage, organisations are already strongly motivated to embrace digital and operational resilience. DORA not only brings a drive toward consistency and best practice but it also elevates corporate and market-wide resilience strategies by demanding an overarching business level perspective.
Five Pillars
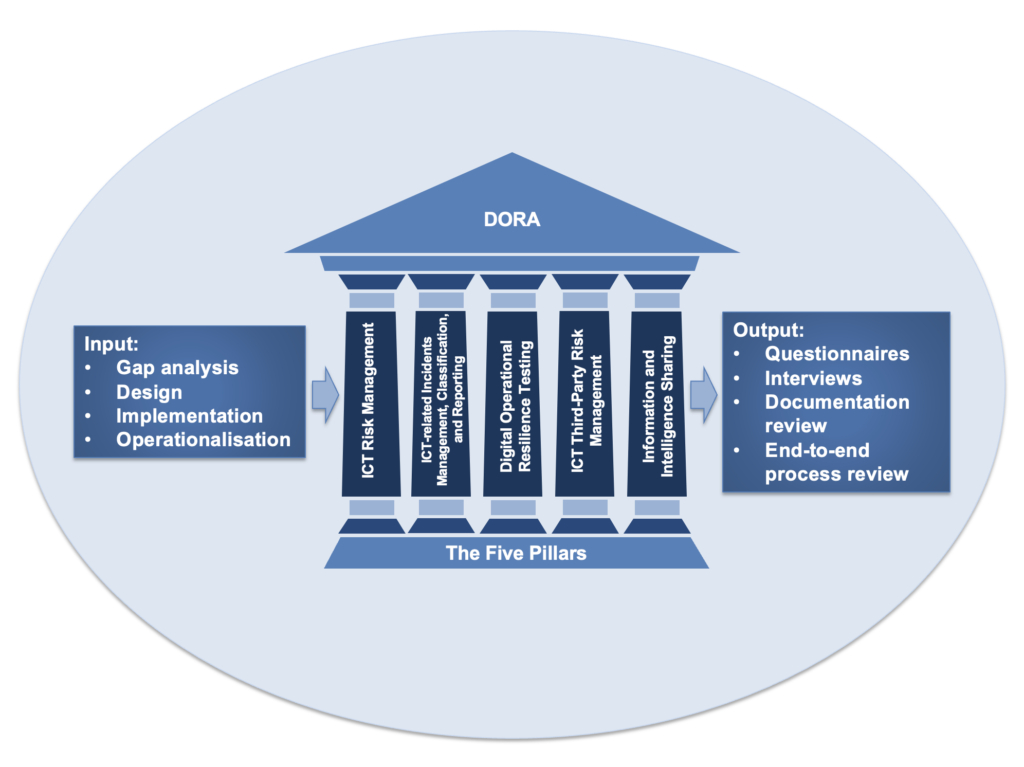
The DORA framework comprises five pillars: risk management, incident reporting, digital operational resilience testing, ICT third-party risk management and information and intelligence sharing. Organisations will have already put in place a lot of the risk management, incident reporting and digital operational resilience testing – although typically this will have occurred at business unit level and must now be reviewed from an organisation-wide perspective. Furthermore, digital operational resilience testing now includes different gradients of seriousness relating to critical functions.
A holistic view of the organisation’s ICT infrastructure and risk framework is vital to bring together the isolated, business unit specific policies that have been deployed to date. If these existing models are not adequate to align with DORA, rework will be required. Inevitably senior level oversight will be needed, ideally from a Chief Risk Officer, who will work closely with an organisation’s nominated DORA champion. Implications and implementation will vary dependent upon the maturity of each institution’s current resilience posture and specific operational risk profile – and until an organisation starts to assess its position with regards to DORA requirements, the level of rework and
time required to undertake that work will remain unknown.
Managing ICT Risk
One of the most significant changes for financial institutions demanded by DORA is the introduction of explicit contractual provisions with ICT providers. These conditions are clearly outlined within DORA and a basic renegotiation of the contractual terms with any service provider is a fundamental requirement. As long as the ICT provider is willing and able to comply, this process should be fairly self-contained, using the DORA wording to renegotiate matters.
However, the sheer scale of the industry compliance required cannot be underestimated, given over 20,000 financial institutions and ICT providers are in scope for DORA. In addition to contractual renegotiation, including guidance on terminating relationships, financial institutions must also maintain a register of information related to contractual arrangements on the services provided by ICT third parties. Firms must also distinguish those ICT third parties supporting critical or important functions, ensure that financial entities can exit relationships without disrupting business activities, surface any conflicts of interest and identify sources of concentration risks.
This is clearly not an overnight exercise and while it is likely over time that some form of DORA certification will be introduced for ICT providers to support a more streamlined compliance process, that is still in the future.
Propagating Best Practice
Naturally, organisations want to align DORA compliance to the furthest extent possible with existing practice. This will require technical skills, insight into operational and market risk and an understanding of the impact of data breach and/or service interruption on the business. If this expertise is not available internally, it is important to look to the market for support, especially given the limited timeframe.
Indeed, with DORA affecting not only the top tier financial institutions and large ICT providers, but any organisation of any size operating within the European financial markets, there is an essential role for external providers to play. Small and medium sized organisations will lack the resources to handle extensive change management programmes, and the adoption of streamlined processes for DORA compliance will be key in ensuring every affected business can achieve the level of digital resilience required to remain competitive within this market.
The important steps organisations will need to consider in adopting DORA compliance include:-
(i) Initiating a gap analysis between the existing practice and the target operating model of full DORA compliance
(ii) Design of the new infrastructure
(iii) Implementation; and
(iv) Operationalisation.
Firms should consider how best to achieve these steps with the resources they have available including internal questionnaires, stakeholder interviews and end-to-end documentation and process reviews. The new legal requirements should ultimately be interwoven into the existing landscape of the organisation’s technology, data flows and network infrastructure.
The additional challenge for the market is that this expertise is highly specialized, demanding both an in-depth knowledge of financial institutions’ operational and data infrastructure and an understanding of DORA’s legal changes. There is, by default, a limited pool of talent offering this combined expertise; even fewer that can also provide the support in the vital process of ensuring all legal contracts with ICT third parties are renegotiated in line with the DORA requirements.
Conclusion
At a time of escalating, global geopolitical instability and the rise of state-sponsored cyber-attacks designed to destabilise European economies, the introduction of DORA reinforces the fact that digital resilience is a serious, board level concern. And while many organisations should have in place robust policies, DORA’s focus on business level rather than department level strategy will demand a new level of strategic oversight and commitment from the Chief Risk Officer. With the additional scrutiny required for third party ICT providers, achieving DORA compliance is not a simple tick box exercise.
The deadline is less than 12 months away, giving organisations a limited timespan to achieve compliance. It vital to quickly undertake due diligence to identify potential shortcomings in compliance and assess the level of external input and internal resources required to address those gaps and undertake the rework required.
And to be honest, why wait for the deadline? When achieving best practice will deliver significant operational benefits over and above DORA compliance by reducing the risk of breach or compromise, the benefits are clear.
